Sophos
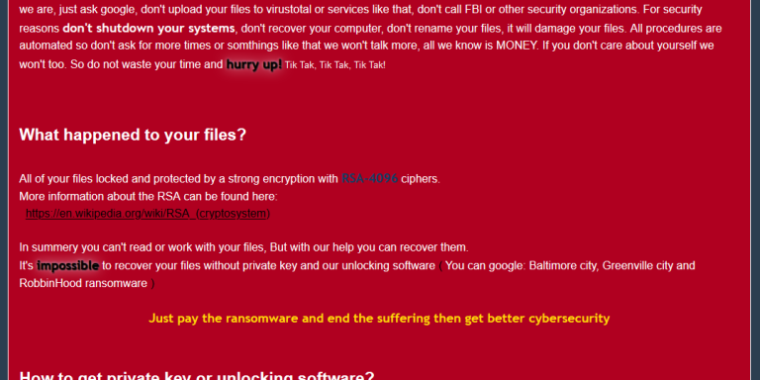
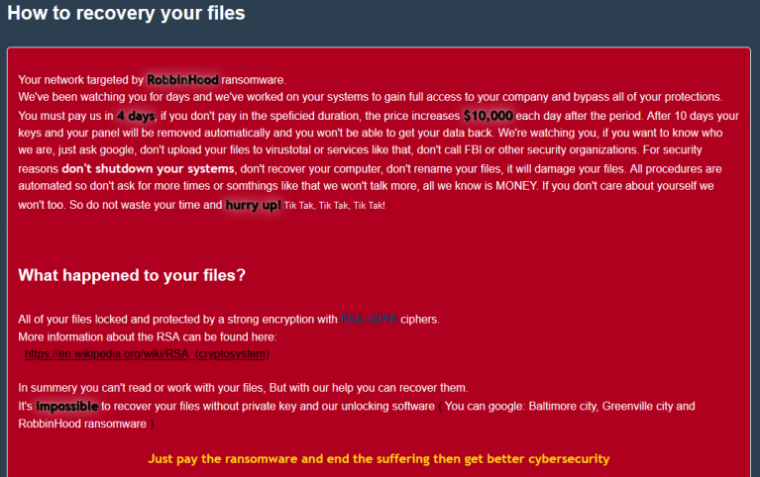
Attackers behind one of many world’s extra damaging items of ransomware have discovered a brand new solution to defeat defenses which may in any other case forestall the assault from encrypting information: putting in a buggy driver first after which hacking it to burrow deeper into the targeted pc.
The ransomware in this case is RobbinHood, identified for taking down the town of Baltimore networks and techniques in Greenville, North Carolina. When networks aren’t protected by strong end-point defenses, RobbinHood can simply encrypt delicate information as soon as a vulnerability has allowed the malware to achieve a toehold. For networks which might be higher fortified, the ransomware has a tougher time.
Now, RobbinHood has discovered a solution to defeat these defenses. In two current assaults, researchers from safety agency Sophos mentioned, the ransomware has used its entry to a targeted machine to put in a driver, from Taiwan-based motherboard producer Gigabyte, that has a identified vulnerability in it. Regardless of the vulnerability that led to the motive force being deprecated, it retains the cryptographic signature required for it to run in the extremely delicate Windows area often called the Kernel.
With the benign however buggy GDRV.SYS driver from Gigabyte put in, RobbinHood exploited the vulnerability to achieve the flexibility to learn and write to nearly any reminiscence area the attackers selected. The RobbinHood exploit modified a single byte to disable the Windows requirement that drivers be signed. With that, RobbinHood put in its personal unsigned driver that used its extremely privileged kernel entry to kill processes and information belonging to endpoint safety merchandise. The superior standing of the motive force gave it larger skill than different methods to make sure the targeted processes are completely stopped.
The Sophos put up didn’t determine the vulnerability or vulnerabilities that RobbinHood used to achieve preliminary entry to the targeted machines. In a message, nonetheless, Sophos researcher Mark Lohman mentioned the preliminary exploit targeted an account with administrative privileges, a feat that allowed a file named STEEL.EXE to run. Nevertheless that was achieved, the ransomware then dropped a file named STEELE.EXE onto the machine and obtained it to run.
Lowman and fellow Sophos researcher Andrew Brandt wrote in the put up:
With out diving into the ransomware or information encryption itself, we’re going to concentrate on the module with which the adversaries can kill encountered endpoint safety software program. This a part of the assault consists of a number of information embedded in STEEL.EXE. All of those information are extracted to C:WINDOWSTEMP
STEEL.EXE Kill software That is the applying that kills the processes and information of safety merchandise, utilizing kernel drivers. ROBNR.EXE Driver installer Deploys each the benign, signed third-party driver, and the criminals’ unsigned kernel driver. As soon as deployed, the unsigned driver will get loaded by abusing a identified vulnerability in the third-party driver. GDRV.SYS Weak kernel driver A benign however outdated Authenticode-signed driver that accommodates a vulnerability. RBNL.SYS Malicious kernel driver The malicious driver that may kill processes and delete information from kernel house. PLIST.TXT Listing of processes (and their related information) to destroy It is a textual content file containing the names of the functions the malicious driver will kill and delete. This textual content file just isn’t embedded in STEEL.EXE and could also be tailor-made to the sufferer’s atmosphere.
STEEL.EXE
The STEEL.EXE software kills the processes and deletes the information of safety functions. With a view to do that, STEEL.EXE deploys a driver. The driving force runs in kernel mode and is due to this fact optimally positioned to take out processes and information with out being hindered by safety controls like endpoint safety. Although they run underneath NT AUTHORITY/SYSTEM, most elements of an endpoint safety product run in consumer house.
The STEEL.EXE software first deploys ROBNR.EXE, which installs the malicious unsigned driver RBNL.SYS.
As soon as this driver is put in, STEEL.EXE reads the PLIST.TXT file and instructs the motive force to delete any software listed in PLIST.TXT, then killing their related processes. If the method was operating as a service, the service can now not routinely restart because the related file has been deleted.
As soon as the STEEL.EXE course of exits, the ransomware program can carry out its encryption assault with out being hindered by the safety functions which have been taken out decisively.
ROBNR.EXE
This software is dropped to the disk by STEEL.EXE. It is a handy software that drops and installs each the susceptible GDRV.SYS driver, and the malicious RBNL.SYS driver.
64-bit Windows computer systems have a mechanism referred to as driver signature enforcement which implies that Windows solely permits drivers to be loaded which have been correctly signed by each the producer and Microsoft. It is a requirement for all drivers in order to be loaded on 64-bit variations of Windows.
The malware authors didn’t trouble to signal their malicious driver because it entails buying a certificates. Additionally, a bought certificates could be revoked by the certificates authority inflicting the motive force to now not work, as it can now not be accepted by Windows.
As an alternative, the malware authors selected a distinct route. The correctly signed third social gathering GDRV.SYS driver accommodates a privilege escalation vulnerability because it permits studying and writing of arbitrary reminiscence. The malware authors abuse this vulnerability in order to (briefly) disable driver signature enforcement in Windows – on-the-fly, in kernel reminiscence. As soon as driver signature enforcement is disabled, the attackers are capable of load their unsigned malicious driver.
The vulnerability in the Gigabyte driver is tracked as CVE-2018-19320. After initially saying the motive force was unaffected by the flaw, Gigabyte officers ultimately acknowledged the flaw and discontinued using the motive force. Regardless of the demise of the motive force, it has remained signed and trusted by all supported variations of Windows.
Microsoft officers declined to talk on the file about their coverage for revoking trust in software program that’s deprecated for safety causes. On background, an worker with Microsoft’s exterior PR agency mentioned that typically, the corporate has certificates revoked solely when the certificates itself has been compromised, which there’s no proof occurred in this case.
Revocations may end up in severe collateral injury when different, non-vulnerable software program is signed utilizing the identical certificates, the worker wrote in an electronic mail. The background assertion additionally famous that to take advantage of the Gigabyte driver, an attacker would first must compromise the targeted system.
The Sophos put up mentioned that there are different Windows-trusted drivers with identified vulnerabilities that may very well be used the identical means Gigabyte’s GDRV.SYS was used. The record included signed drivers from VirtualBox (CVE-2008-3431), Novell (CVE-2013-3956), CPU-Z (CVE-2017-15302), and ASUS (CVE-2018-18537). Whereas the Gigabyte driver could be the first identified occasion, it very nicely is probably not the final.