With the title Smarter, you may count on a network-connected kitchen equipment maker to be, effectively, smarter than firms promoting typical home equipment. However within the case of the Smarter’s Web-of-things coffee maker, you’d be unsuitable.
Safety issues with Smarter merchandise first got here to mild in 2015, when researchers at London-based safety agency Pen Take a look at companions discovered that they may recuperate a Wi-Fi encryption key used within the first model of the Smarter iKettle. The identical researchers discovered that model 2 of the iKettle and the then-current model of the Smarter coffee maker had further issues, together with no firmware signing and no trusted enclave contained in the ESP8266, the chipset that fashioned the brains of the gadgets. The outcome: the researchers confirmed a hacker may in all probability change the manufacturing unit firmware with a malicious one. The researcher EvilSocket additionally carried out a full reverse engineering of the system protocol, permitting reomote management of the system.
Two years in the past, Smarter launched the iKettle model Three and the Coffee Maker model 2, mentioned Ken Munro, a researcher who labored for Pen Take a look at Companions on the time. The up to date merchandise used a new chipset that mounted the issues. He mentioned that Smarter by no means issued a CVE vulnerability designation, and it did not publicly warn prospects to not use the previous one. Information from the Wigle community search engine reveals the older coffee makers are nonetheless in use.
As a thought experiment, Martin Hron, a researcher at safety firm Avast, reverse engineered one of many older coffee makers to see what sorts of hacks he may do with it. After simply a week of effort, the unqualified reply was: fairly a lot. Particularly, he may set off the coffee maker to activate the burner, dispense water, spin the bean grinder, and show a ransom message, all whereas beeping repeatedly. Oh, and by the best way, the one approach to cease the chaos was to unplug the ability twine. Like this:
What a hacked coffee maker seems like
“It’s doable,” Hron mentioned in an interview. “It was completed to level out that this did occur and will occur to different IoT gadgets. This is a good instance of an out-of-the-box downside. You do not have to configure something. Normally, the distributors don’t take into consideration this.”
What do you imply “out-of-the-box”?

When Hron first plugged in his Smarter coffee maker, he found that it instantly acted as a Wi-Fi entry level that used an unsecured connection to speak with a smartphone app. The app, in flip, is used to configure the system and, ought to the person select, join it to a house Wi-Fi community. With no encryption, the researcher had no downside studying how the cellphone managed the coffee maker and, since there was no authentication both, how a rogue cellphone app may do the identical factor.
That functionality nonetheless left Hron with solely a small menu of instructions, none of them particularly dangerous. So he then examined the mechanism the coffee maker used to obtain firmware updates. It turned out they had been obtained from the cellphone with—you guessed it—no encryption, no authentication, and no code signing.
These obvious omissions created simply the chance Hron wanted. For the reason that newest firmware model was saved contained in the Android app, he may pull it onto a laptop and reverse engineer it utilizing IDA, a software program analyzer, debugger, and disassembler that’s one in all a reverse engineer’s greatest mates. Nearly instantly, he discovered human-readable strings.
“From this, we may deduce there is no encryption, and the firmware is in all probability a ‘plaintext’ picture that is uploaded immediately into the FLASH reminiscence of the coffee maker,” he wrote on this detailed weblog outlining the hack.
Taking the insides out
To really disassemble the firmware—that is, to remodel the binary code into the underlying meeting language that communicates with the {hardware}, Hron needed to know what CPU the coffee maker used. That required him to take aside the system internals, discover the circuit board, and determine the chips. The 2 photographs under present what he discovered:
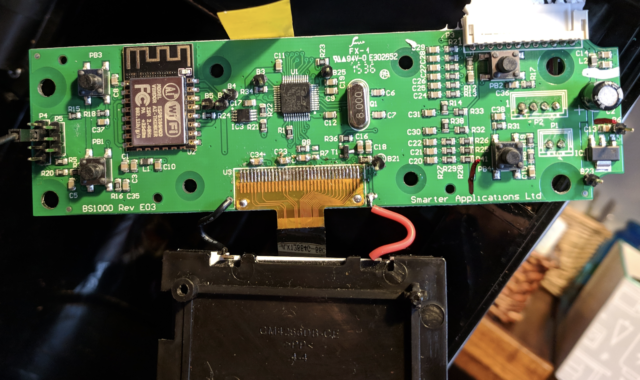
Avast

Avast
With the flexibility to disassemble the firmware, the items began to return collectively. Hron was in a position to reverse an important features, together with those that test if a carafe is on the burner, trigger the system to beep, and—most significantly—set up an replace. Under is a block diagram of the coffee maker’s principal parts:
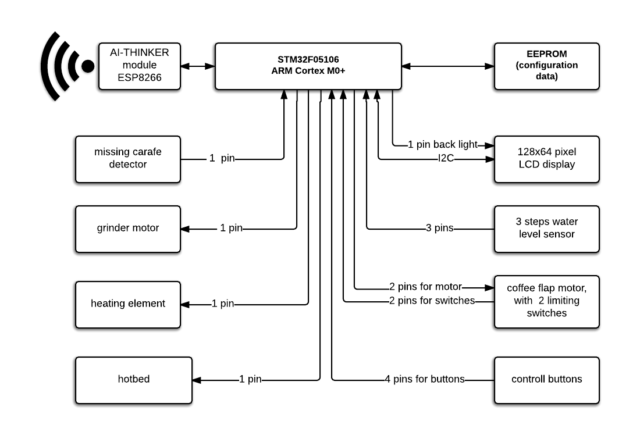
Hron ultimately acquired sufficient info to put in writing a python script that mimicked the replace course of. Utilizing a barely modified model of the firmware, he found it labored. This was his “hiya world” of types:

Avast
Freak out any person
The subsequent step was to create modified firmware that did one thing much less innocuous.
“Initially, we needed to show the truth that this system may mine cryptocurrency,” Hron wrote. “Contemplating the CPU and structure, it is actually doable, however at a velocity of 8MHz, it doesn’t make any sense because the produced worth of such a miner can be negligible.”
So the researcher settled on one thing else—a machine that might precise a ransom if the proprietor needed it to cease spectacularly malfunctioning the best way proven within the video. With the good thing about some unused reminiscence area within the silicon, Hron added strains of code that induced all of the commotion.
“We thought this may be sufficient to freak any person out and make it a very tense expertise. The one factor the person can do at that time is unplug the coffee maker from the ability socket.”
As soon as the working replace script and modified firmware is written and loaded onto an Android cellphone (iOS can be a lot more durable, if not prohibitively so due to its closed nature), there are a number of methods to hold out the assault. The simplest is to search out a weak coffee maker inside Wi-Fi vary. Within the occasion the system hasn’t been configured to hook up with a Wi-Fi community, this is so simple as in search of the SSID that’s broadcast by the coffee maker.
Beachhead
As soon as the system connects to a house community, this advert hoc SSID required to configure the coffee maker and provoke any updates is not accessible. Essentially the most easy approach to work round this limitation can be if the attacker knew a coffee maker was in use on a given community. The attacker would then ship the community a deauthorization packet that might trigger the coffee maker to disconnect. As quickly as that occurs, the system will start broadcasting the advert hoc SSID once more, leaving the attacker free to replace the system with malicious firmware.
A extra opportunistic variation of this vector can be to ship a deauthorization packet to each SSID inside Wi-Fi vary and wait to see if any advert hoc broadcasts seem (SSIDs are at all times “Smarter Coffee:xx,” the place xx is the identical because the lowest byte of the system’s MAC tackle).
The limitation of this assault, will probably be apparent to many, is that it really works solely when the attacker can find a weak coffee maker and is inside Wi-Fi vary of it. Hron mentioned a approach round this is to hack a Wi-Fi router and use that as a beachhead to assault the coffee maker. This assault could be completed remotely, but when an attacker has already compromised the router, the community proprietor has worse issues to fret about than a malfunctioning coffee maker.
In any occasion, Hron mentioned the ransom assault is only the start of what an attacker may do. With extra work, he believes, an attacker may program a coffee maker—and presumably different home equipment made by Smarter—to assault the router, computer systems, or different gadgets linked to the identical community. And the attacker may in all probability do it with no overt signal something was amiss.
Placing it in perspective
Due to the constraints, this hack isn’t one thing that represents a actual or rapid menace, though for some folks (myself included), it’s sufficient to steer me away from Smarter merchandise, not less than so long as present fashions (the one Hron used is older) don’t use encryption, authentication, or code signing. Firm representatives didn’t instantly reply to messages asking.
Relatively, as famous on the prime of this publish, the hack is a thought experiment designed to discover what’s doable in a world the place coffee machines, fridges, and all different method of house gadgets all connect with the Web. One of many fascinating issues concerning the coffee machine hacked right here is that it’s not eligible to obtain firmware updates, so there’s nothing homeowners can do to repair the weaknesses Hron discovered.
Hron additionally raises this essential level:
Moreover, this case additionally demonstrates one of the vital regarding points with trendy IoT gadgets: “The lifespan of a typical fridge is 17 years, how lengthy do you suppose distributors will assist software program for its sensible performance?” Positive, you can nonetheless use it even when it’s not getting updates anymore, however with the tempo of IoT explosion and unhealthy perspective to assist, we are creating a military of deserted weak gadgets that may be misused for nefarious functions corresponding to community breaches, information leaks, ransomware assault and DDoS.
There’s additionally the issue of understanding what to do concerning the IoT explosion. Assuming you get an IoT gadget in any respect, it’s tempting to suppose that the, uh, smarter transfer is to easily not join the system to the Web in any respect and permit it to function as a regular, non-networked equipment.
However within the case of the coffee maker right here, that might truly make you extra weak, since it might simply broadcast the advert hoc SSID and, in so doing, save a hacker a few steps. In need of utilizing an old school coffee maker, the higher path can be to attach the system to a digital LAN, which these days often includes utilizing a separate SSID that’s partitioned and remoted in a laptop community on the information hyperlink layer (OSI layer 2).
Hron’s write-up linked above gives greater than 4,000 phrases of wealthy particulars, a lot of which are too technical to be captured right here. It needs to be required studying for anybody constructing IoT gadgets.
Story up to date so as to add second and third paragraphs explaining earlier work Hron’s hack builds upon.
Itemizing picture by Avast